About proxies
Proxy is generally used to perform a man-in-the-middle attack. But not to just perform the pure MITM attack, it’s convenient to view, analyze and modify the data flow generated by the APPs with a proxy. It’s getting difficult to catch the network traffic on mobile and I’m here to talk about the proposals.
Methods to do that
There are 4 methods listed below, and there are certainly other methods exist in this world, but they’re beyond the scope of this post.
It’s simple, just get into the settings and set the proxy and port to your own server, and it’s done.
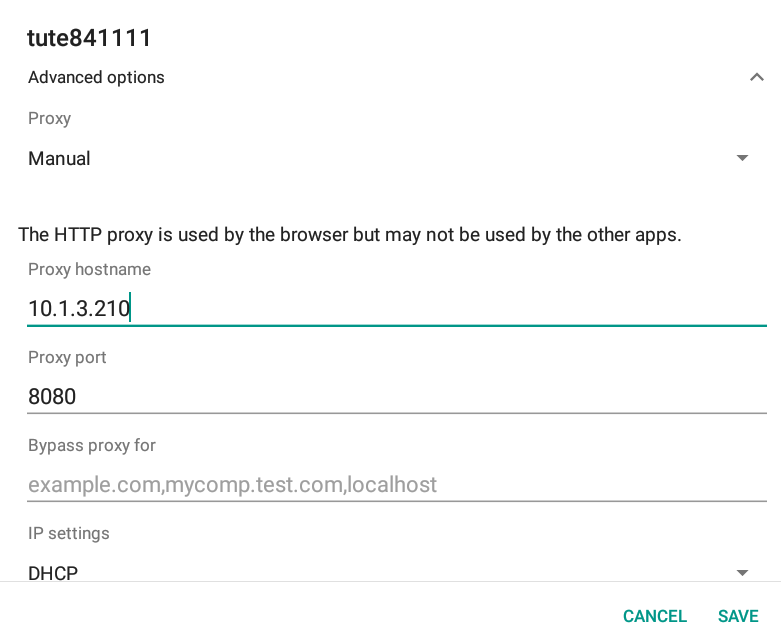
This is recommended for most users, but it doesn’t work if the APP doesn’t allow system proxy.
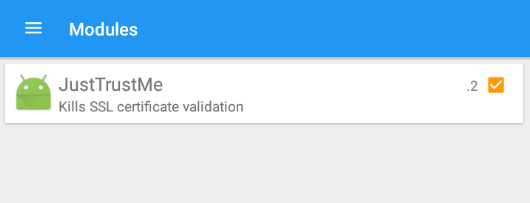
Xposed is a framework used to hook functions in android and JustTrustMe is a module disables SSL certificate checking. (https://github.com/Fuzion24/JustTrustMe)
It aims at solving the HTTPS proxy problem. It’s a powerful tool if you want to view the network traffic of APPs which does certificate pinning.
Download Xposed installer(https://repo.xposed.info/module/de.robv.android.xposed.installer) and get it installed on your android device. The JustTrustMe binary can be downloaded from https://github.com/Fuzion24/JustTrustMe/releases/latest, Then install it:
1 | adb install ./JustTrustMe.apk |
You can now find that JustTrustMe exists in your Xposed modules.
This is a little bit tricky, it’s briefly illustrated below:
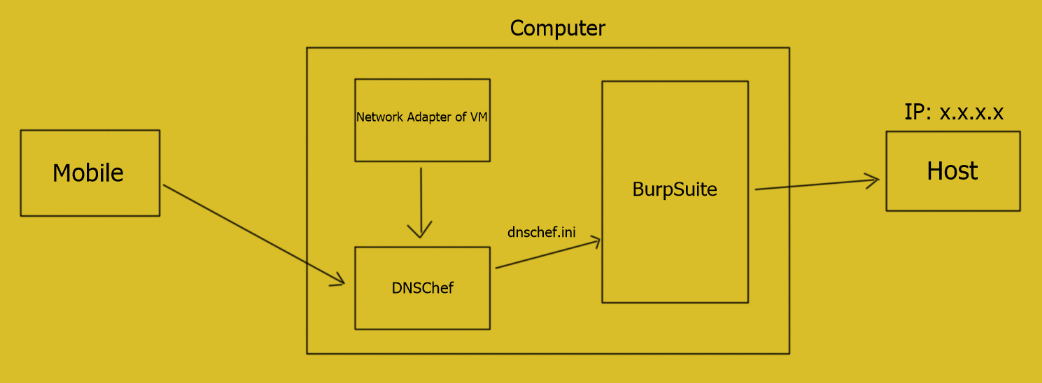
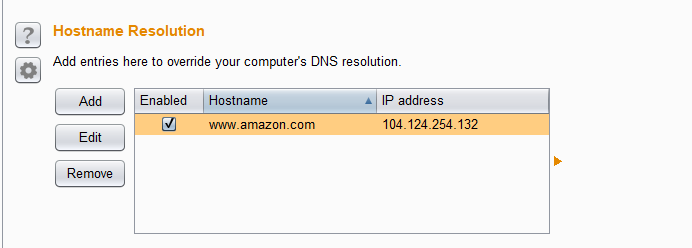
An elegant tool used here is DNSChef. (https://github.com/iphelix/dnschef) , modify the dnschef.ini file to adapt to your needs and configure the nameserver and the listening interface. The content changed here is the A records.
1 | *.amazon.com=10.1.3.210 |
Start up a DNSChef server:
1 | python dnschef.py --file=dnschef.ini --nameservers=8.8.8.8 --interface=127.0.0.1 |
If you’re using APPs within an android virtual machine, remember to change the nameserver of the network adapter you’re using to the loopback interface, then all the DNS requests to your machine will resend to DNSChef.
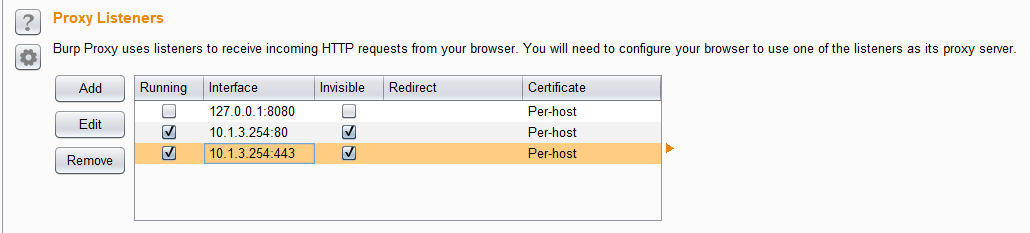
Open listeners in BurpSuite:
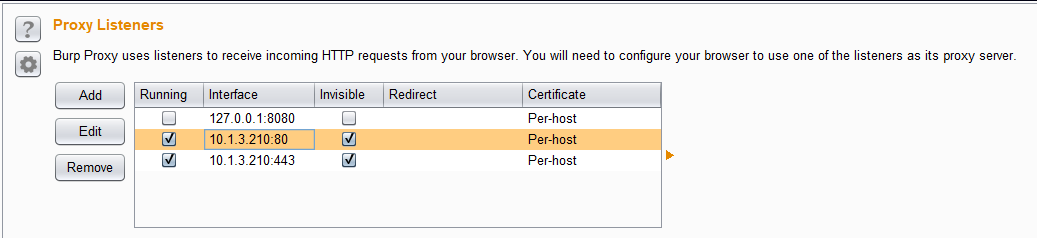
Find out the target IP of your requested hosts so that BurpSuite can follow the DNS resolution.
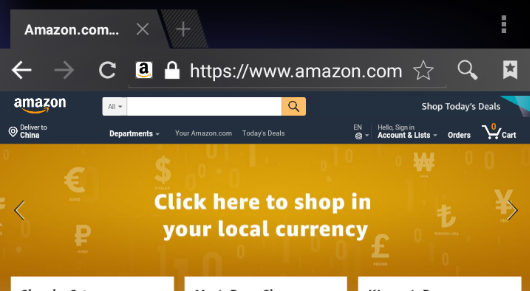
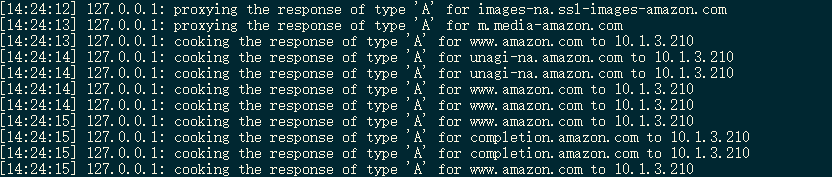
Assuming that you send a request to www.amazon.com you can get ordinary responses like this:
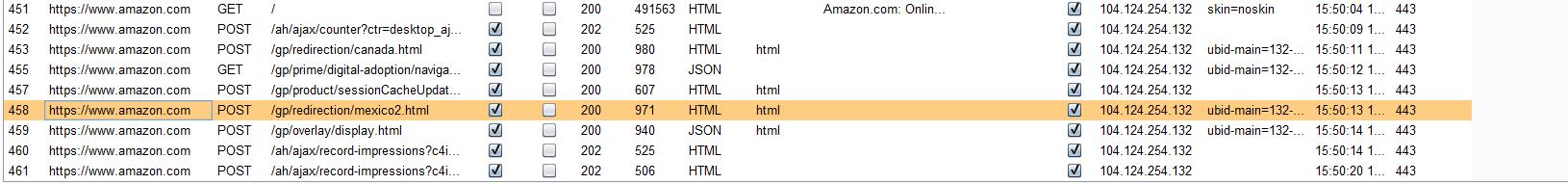
It just does simple traffic forwarding between devices, the problem of SSL certificate pinning should be handled by other tools.
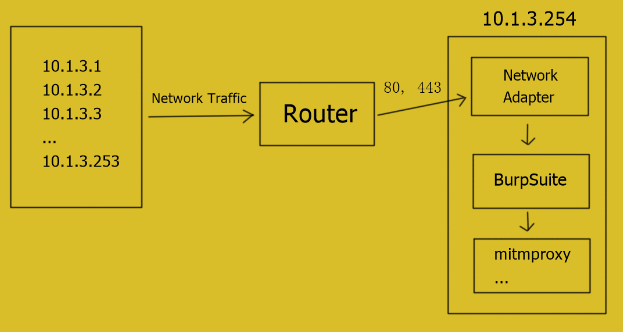
If you are using a router which allows forwarding ports in GUI, that will be much easier. And you can also install firmware into your router, OpenWrt is one of the choices. OpenWrt Project is a Linux operating system targeting embedded devices and you can execute shell directives on your router with it.
For ports forwarding:
1 | iptables -t nat -A PREROUTING -m iprange --src-range 10.1.3.1-10.1.3.253 -p tcp --dport 80 -j DNAT --to-destination 10.1.3.254:80 |
This directive will forward all the network traffic of ip 10.1.3.1~10.1.3.253 at port 80, 443 to ip 10.1.3.254 at port 80, 443.
Make it clear:
Open the BurpSuite listeners:
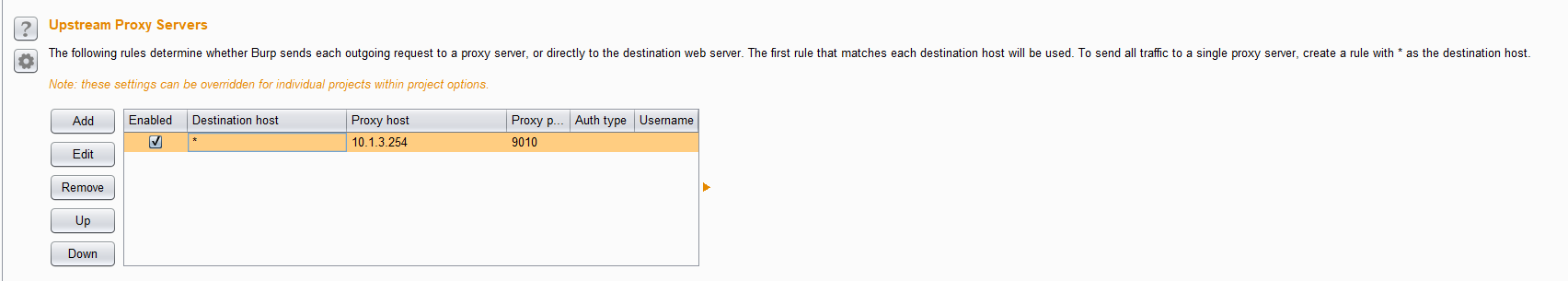
All that network traffic can be sent directly or through a proxy like mitmproxy(https://github.com/mitmproxy/mitmproxy) listened at port 9010, it’s necessary if you would like to make some changes to the packets.
What else?
Those proposals mentioned above can handle almost 90% of the situations we will encounter. If it doesn’t work, some tools work at IP based network may be helpful, such as bettercap.(https://github.com/bettercap/bettercap)